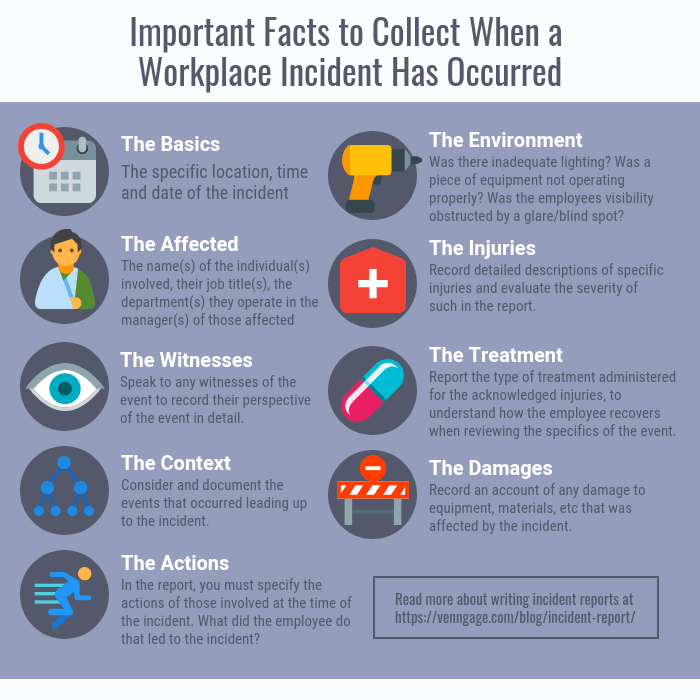
Which incident type do these characteristics indicate? This question is crucial for incident responders and analysts as it helps them understand the nature of an incident and determine the appropriate response. By examining the characteristics of an incident, such as its severity, impact, and the assets involved, responders can gain valuable insights into the type of incident they are dealing with.
The analysis of incident characteristics can help identify patterns and trends, which can inform incident response and prevention strategies. By understanding the relationship between incident characteristics and incident types, responders can develop more effective and targeted response plans.
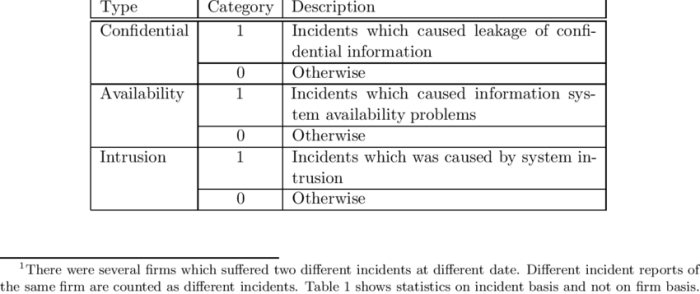
Incident Characteristics: Which Incident Type Do These Characteristics
Incident characteristics are the attributes that describe an incident. They can be used to categorize incidents, determine their severity, and identify trends. Some common incident characteristics include:
- Type: The type of incident, such as a security breach, data loss, or system outage.
- Severity: The severity of the incident, such as low, medium, or high.
- Impact: The impact of the incident, such as financial loss, reputational damage, or loss of customer data.
- Source: The source of the incident, such as an internal employee, an external hacker, or a natural disaster.
- Time: The time of the incident, such as the date and time it occurred.
- Location: The location of the incident, such as the physical location or the network address.
Incident Types
The type of incident is one of the most important characteristics to consider. The type of incident will determine the response and recovery procedures that need to be followed.
Some common incident types include:
- Security breaches: A security breach is an unauthorized access to a computer system or network. Security breaches can be caused by a variety of factors, such as phishing attacks, malware, or social engineering.
- Data loss: Data loss is the loss of data from a computer system or network. Data loss can be caused by a variety of factors, such as hardware failures, software errors, or human error.
- System outages: A system outage is a period of time when a computer system or network is unavailable. System outages can be caused by a variety of factors, such as power outages, hardware failures, or software errors.
Incident Analysis, Which incident type do these characteristics
Incident analysis is the process of examining the characteristics of an incident to determine its cause and impact. Incident analysis can be used to identify trends, develop prevention strategies, and improve response procedures.
There are a number of different techniques that can be used to perform incident analysis. Some common techniques include:
- Root cause analysis: Root cause analysis is a technique that is used to identify the underlying cause of an incident. Root cause analysis can be performed using a variety of tools and techniques, such as the 5 Whys, the Fishbone diagram, and the Fault Tree Analysis.
- Trend analysis: Trend analysis is a technique that is used to identify patterns and trends in incident data. Trend analysis can be used to identify emerging threats, develop prevention strategies, and improve response procedures.
- Risk assessment: Risk assessment is a technique that is used to identify and assess the risks associated with an incident. Risk assessment can be used to prioritize incidents, develop mitigation strategies, and allocate resources.
Incident Response and Prevention
Incident response is the process of responding to an incident in order to minimize its impact and restore normal operations. Incident response plans should be developed in advance and should be tailored to the specific needs of the organization.
Incident prevention is the process of taking steps to prevent incidents from occurring. Incident prevention strategies should be based on the results of incident analysis and should be tailored to the specific risks faced by the organization.
There are a number of different strategies that can be used to prevent and respond to incidents. Some common strategies include:
- Security awareness training: Security awareness training is a program that is designed to educate employees about the risks of security breaches and how to protect themselves and the organization from these risks.
- Vulnerability management: Vulnerability management is a process that is used to identify and patch vulnerabilities in computer systems and networks.
- Backup and recovery: Backup and recovery is a process that is used to create and maintain backups of important data. Backups can be used to restore data in the event of a data loss incident.
Common Queries
What are the most common incident characteristics?
The most common incident characteristics include severity, impact, and the assets involved.
How can incident characteristics help determine the incident type?
Incident characteristics can help determine the incident type by providing insights into the nature and scope of the incident.
What is the importance of incident analysis?
Incident analysis is important because it helps identify patterns and trends, which can inform incident response and prevention strategies.